Block abuse of exploited vulnerable signed drivers
A vulnerable signed driver is a type of device driver that has been digitally signed by the manufacturer, but contains security vulnerabilities that can be exploited by attackers to gain unauthorized access to a system or perform other malicious actions.
Digital signatures are used to verify the authenticity of a driver and ensure that it comes from a trusted source. However, if a signed driver contains vulnerabilities that can be exploited by attackers, it can still pose a significant security risk to the system.
Attackers can exploit vulnerabilities in signed drivers to bypass security controls, escalate privileges, or execute malicious code on the system. This can allow them to gain access to sensitive data, install malware or perform other malicious activities.
To mitigate the risk of vulnerable signed drivers, it is important to keep all drivers up-to-date with the latest security patches and to only download drivers from trusted sources. Regular vulnerability scanning and security assessments can also help to identify any vulnerable signed drivers that may be present on the system.
Why would you not want to block abuse of exploited vulnerable signed drivers?
There may be some situations where you would not want to immediately block exploited vulnerable signed drivers, depending on the context and risk assessment.
For example, in some cases, an organization may rely on a particular vulnerable signed driver for a critical business function. In such cases, immediately blocking the driver could cause significant disruptions to the organization's operations and negatively impact business continuity.
Moreover, blocking a vulnerable signed driver without a proper replacement could also result in hardware or software compatibility issues that can cause system instability or downtime.
However, it is important to note that leaving an exploited vulnerable signed driver in place without proper safeguards can also pose significant security risks. Attackers can leverage these vulnerabilities to gain unauthorized access to the system or execute malicious code, which can result in data theft, data destruction, or other harmful outcomes.
Therefore, in cases where a vulnerable signed driver must be left in place, organizations should take measures to mitigate the risks associated with the vulnerability, such as limiting access to the system, implementing additional security controls, or closely monitoring the system for signs of exploitation.
In general, the decision to block exploited vulnerable signed drivers should be based on a careful assessment of the risks and benefits, taking into account the criticality of the driver to the organization's operations and the severity of the security risks posed by the vulnerability.
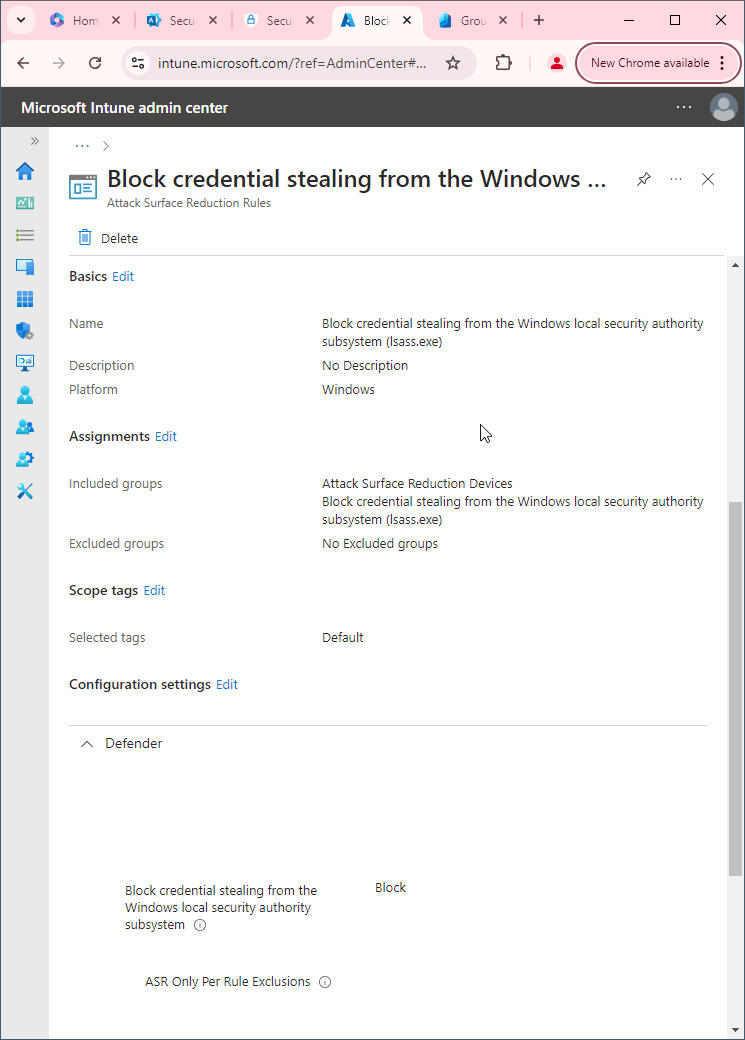
How to block abuse of exploited vulnerable signed drivers
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block abuse of exploited vulnerable signed drivers using Intune.

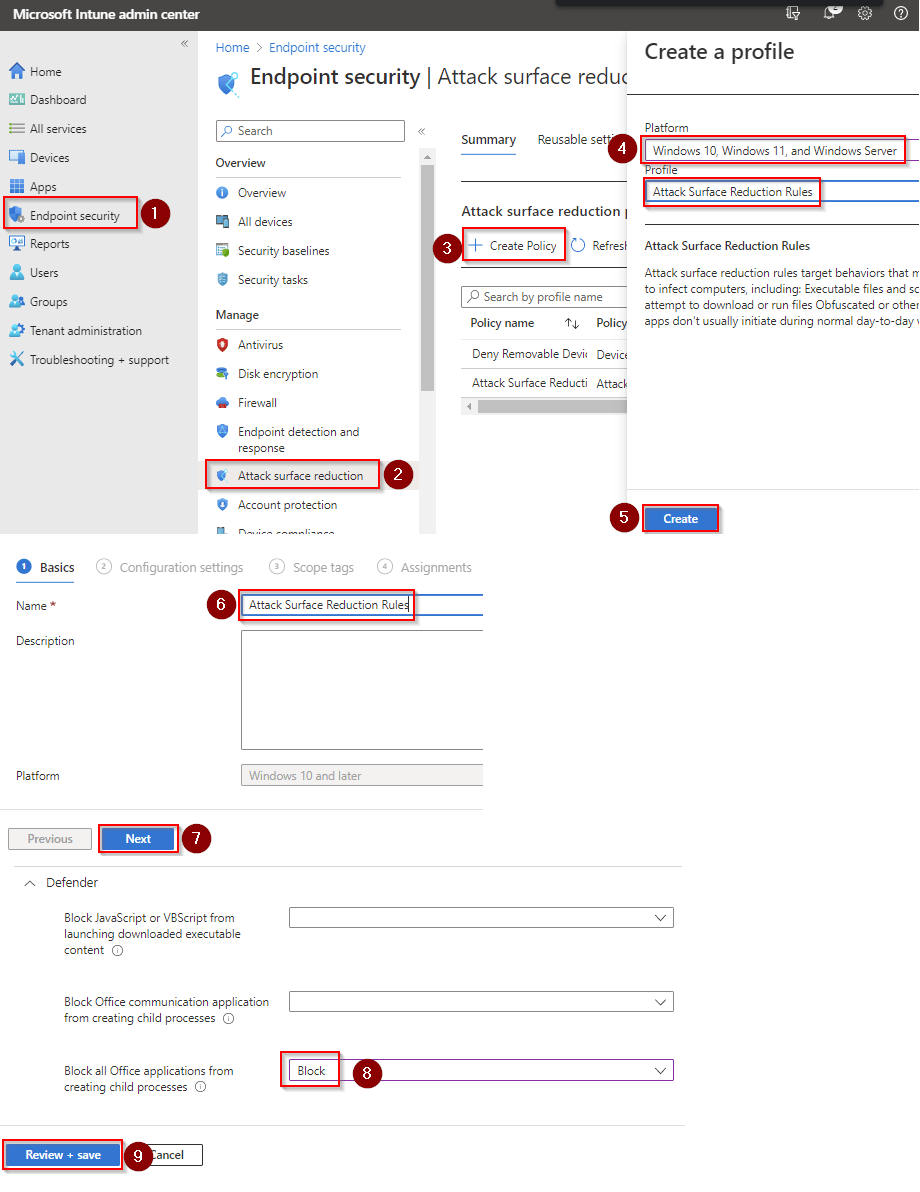
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set
Block abuse of exploited vulnerable signed drivers (Device)to Block. Click Next. - Add your inclusions and exclusions. Click Next > Next > Create.