Block all Office applications from creating child processes
Blocking all Office applications from creating child processes can be a good security practice because it limits the ability of malicious actors to exploit vulnerabilities in those applications.
What are child processes?
Child processes are sub-processes that are spawned by a parent process. Office applications like Microsoft Word or Excel may create child processes to perform certain tasks, such as opening a linked document or performing calculations. However, attackers can potentially use this functionality to run malicious code or execute unauthorized actions by exploiting vulnerabilities in the child process.
By blocking all Office applications from creating child processes, you can prevent these potential exploits from being executed. This is particularly important in environments where security is a critical concern, such as government agencies or financial institutions.
Why would you not want to block child processes?
However, it's important to note that this security measure may also limit some legitimate functionality of the office applications. Therefore, it's essential to carefully evaluate the potential impact before implementing such a measure. Additionally, it should be just one part of a larger security strategy that includes other best practices like software updates, user education, and access control.
How to block all Office applications from creating child processes
Blocking all Office applications from creating child processes can be accomplished in a few different ways, depending on your specific environment and requirements. Here are a few general approaches:
- Intune: If you are using Microsoft 365's Intune then you can easily block Office applications from creating child processes. It's as simple as creating an attack surface reduction rule.
- Group Policy: If you are using a Windows Active Directory environment, you can use Group Policy to block child processes for Office applications. You can create a policy that sets the "Block child processes" option to "Enabled" for the appropriate Office applications. This option can be found in the "User Configuration > Administrative Templates > Microsoft Office [Version] > Security Settings" section of the Group Policy editor.
- AppLocker: AppLocker is a feature in Windows that allows you to create policies that specify which applications are allowed to run on your system. You can create an AppLocker policy that blocks child processes for the appropriate Office applications.
- Third-party tools: There are a variety of third-party tools available that can help you block child processes for specific applications, including Office applications. These tools may offer more granular control over the applications and processes that are affected, as well as additional features like auditing and reporting.
How to block all Office applications from creating child processes using Intune
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that we know our devices are ready, let's go ahead and block Office applications from creating child processes using Intune.

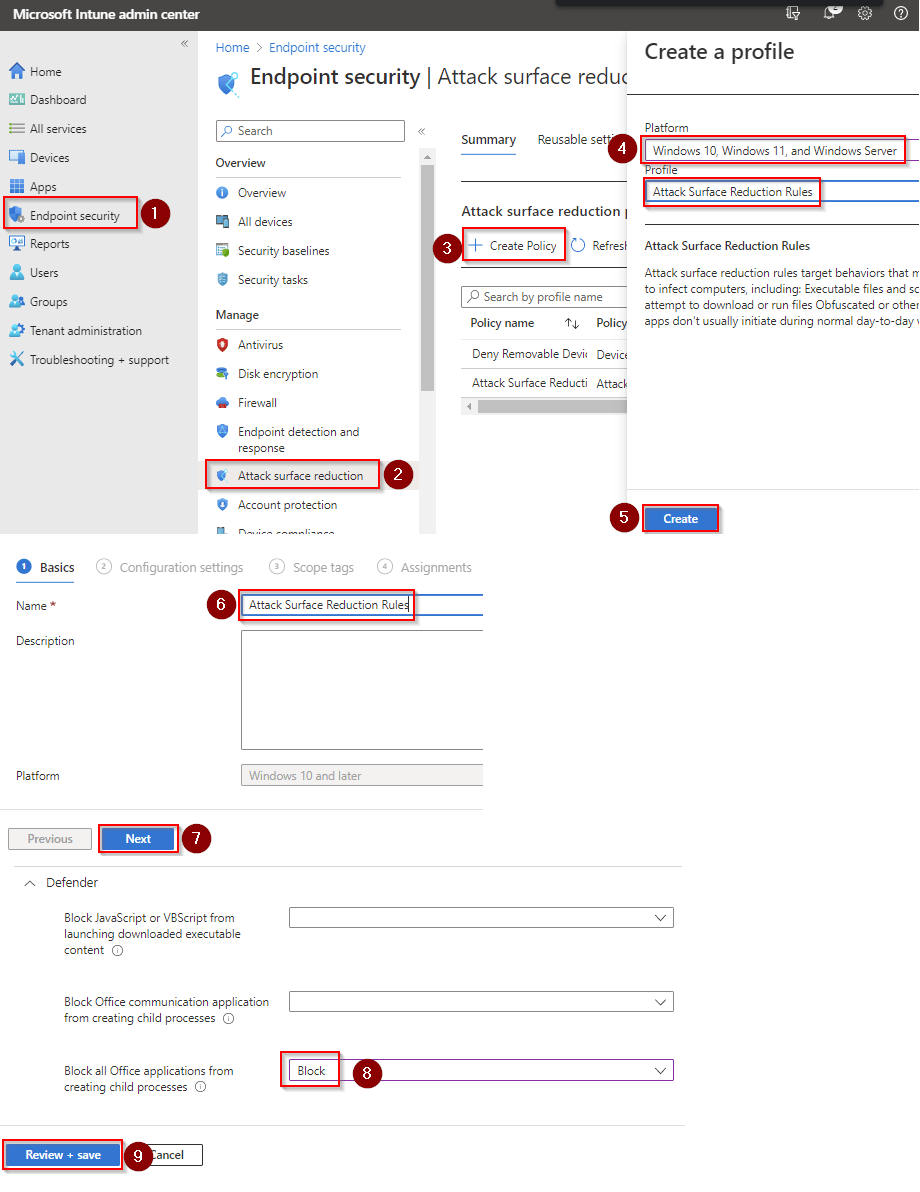
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
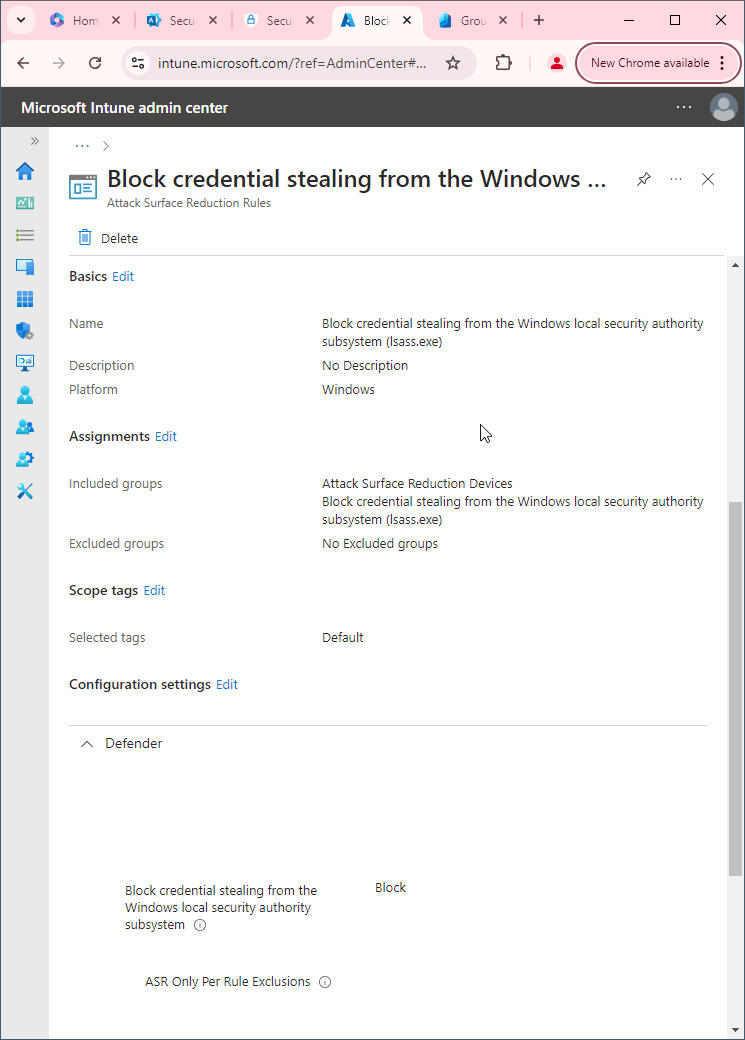
- Set Block all Office applications from creating child processes to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.