Block untrusted and unsigned processes that run from USB
Blocking untrusted and unsigned processes that run from USB drives can be a useful security measure for several reasons:
- Prevent malware infection: Malware can often spread via USB drives, where an attacker may place malicious software that automatically runs when the USB is inserted. By blocking untrusted and unsigned processes from running, you can prevent the execution of malware and reduce the risk of infection.
- Limit the attack surface: Blocking untrusted and unsigned processes from running can help limit the attack surface of a system, by preventing attackers from using USB drives as a method of delivering malicious software or exploits.
- Enforce security policies: If your organization has specific policies in place regarding the use of USB drives or the execution of untrusted or unsigned processes, blocking these processes can help enforce those policies and limit the potential for non-compliance.
- Improve system performance: Untrusted and unsigned processes can consume system resources and impact performance. By blocking these processes, you can help maintain system performance and prevent potential slowdowns or crashes.
It's worth noting that some legitimate applications may run from USB drives, and blocking all untrusted and unsigned processes could potentially impact the functionality of necessary applications. Organizations should evaluate the potential impact on system functionality before implementing this security measure and may choose to implement other measures in conjunction with USB process blocking, such as regular antivirus scans and user education.
Why would you not want to Block untrusted and unsigned processes that run from USB?
There are a few reasons why you might not want to block all untrusted and unsigned processes that run from USB drives:
- Compatibility: Blocking all untrusted and unsigned processes could impact the functionality of legitimate applications that run from USB drives. Some applications may not be signed or may be considered untrusted, even though they are not malicious.
- False positives: There is a risk of false positives, where legitimate processes or applications are mistakenly identified as untrusted or unsigned and are blocked from running.
- User convenience: If employees need to use USB drives regularly as part of their work, blocking all untrusted and unsigned processes could be inconvenient and slow down work processes.
- USB usage policy: Implementing a strict policy regarding USB usage, such as only allowing specific USB drives or requiring all USB drives to be scanned for malware before use, may be a more effective security measure than blocking all untrusted and unsigned processes.
Overall, blocking untrusted and unsigned processes that run from USB drives can be an effective security measure in certain circumstances, but it's important to carefully evaluate the potential impact on system functionality and user convenience before implementing this measure. A balanced approach that includes multiple security measures, such as regular antivirus scans and user education, may be more effective at mitigating the risks associated with USB drives.
How to block untrusted and unsigned processes that run from USB
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that our devices are ready, let's go ahead and block untrusted and unsigned processes that run from USB using Intune.

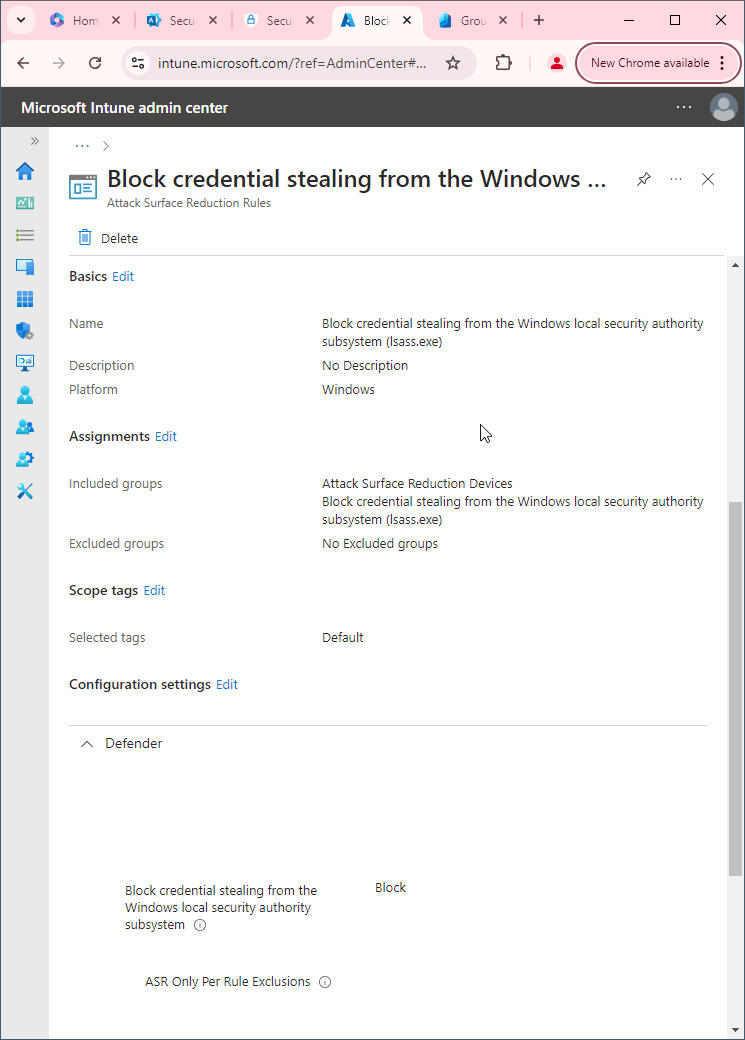
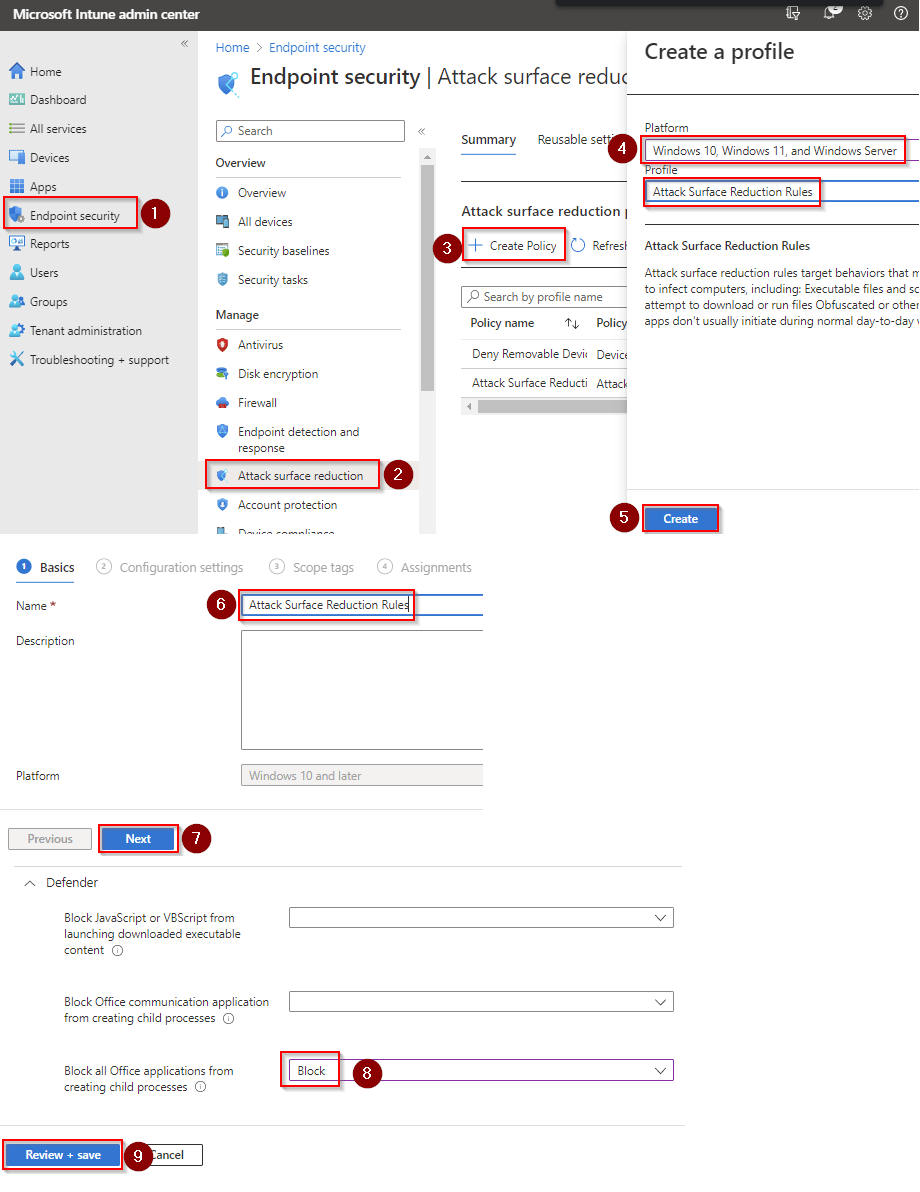
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction.
- Click Create Policy.
- Set Platform to Windows 10 Windows 11, and Windows Server.
- Set Profile to Attack Surface Reduction Rules.
- Click Create.
- Name your policy and click Next.
- Set Block untrusted and unsigned processes that run from USB to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.