Block Win32 API calls from Office macros
Blocking Win32 API calls from Office macros can be a security measure to prevent potential malicious activities. The Win32 API is a collection of functions that allow programs to interact with the operating system and perform various actions such as reading and writing files, accessing the network, and manipulating system settings.
Malicious actors can use Win32 API calls within Office macros to perform unauthorized actions on the user's computer, such as stealing sensitive data, installing malware, or modifying system settings. By blocking Win32 API calls from Office macros, the potential for malicious activities is reduced, as macros are prevented from interacting with the operating system in ways that could compromise security.
Why would you want to allow Win32 API calls from Office macros?
It's important to note that blocking Win32 API calls from Office macros can also impact the functionality of legitimate macros. Therefore, it's important to carefully consider the risks and benefits of blocking API calls and to ensure that your security measures are appropriate for your organization's needs. Typically, I recommend rolling out all policies to one IT admin to test. Then to a pilot group. Then deploy the policy to a larger group and finally to everyone.
Some possible use cases for Win32 API calls from Office macros include:
- Interacting with other programs and applications: With Win32 API calls, you can create macros that can communicate with other programs and applications running on the same machine. This can enable you to automate tasks that involve interacting with multiple applications at once.
- Accessing system resources: Win32 API calls can allow your macros to access system resources such as the file system, registry, and network settings. This can enable you to automate tasks such as backing up files, manipulating registry settings, or configuring network connections.
- Customizing user interface: With Win32 API calls, you can customize the user interface of your Office macros to provide a more streamlined and intuitive user experience. For example, you could create custom dialog boxes, menus, or toolbars that integrate with other Windows applications.
How to block Win32 API calls from Office macros
There are several ways to block Win32 API calls from Office macros. Here are a few options:
- Intune: If you are using Microsoft 365's Intune then you can easily block Office applications from creating child processes. It's as simple as creating an attack surface reduction rule.
- Disable macros: The easiest way to block Win32 API calls from Office macros is to disable macros altogether. You can do this by going to the "Trust Center" in your Office application and selecting "Macro Settings". From there, you can select "Disable all macros with notification" or "Disable all macros except digitally signed macros".
- Group Policy: If you're using an enterprise version of Office, you can use Group Policy to control macro settings for all users in your organization. You can configure Group Policy to block macros from running or to only allow digitally signed macros.
- Third-party tools: There are third-party tools available that can help block Win32 API calls from Office macros. These tools typically work by intercepting API calls and either blocking them or redirecting them to a safe alternative.
How to block Win32 API calls from Office macros using Intune
First, you'll need to make sure Microsoft Defender Antivirus is turned on as the primary antivirus solution, with Real-Time Protection enabled. To verify Defender Antivirus is turned on with real-time protection enabled go to Security recommendations and search for "Turn on real-time protection". From there click "Turn on real-time protection". Finally, click Exposed devices.

Now that we know our devices are ready, let's go ahead and block Win32 API calls from Office macros.

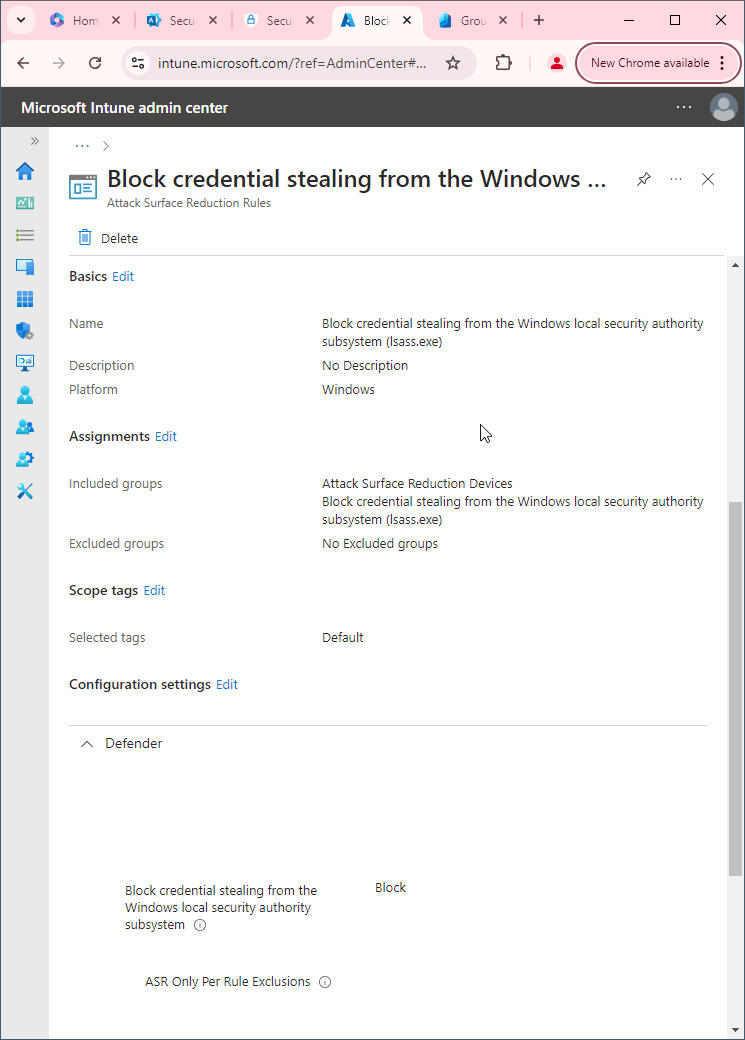
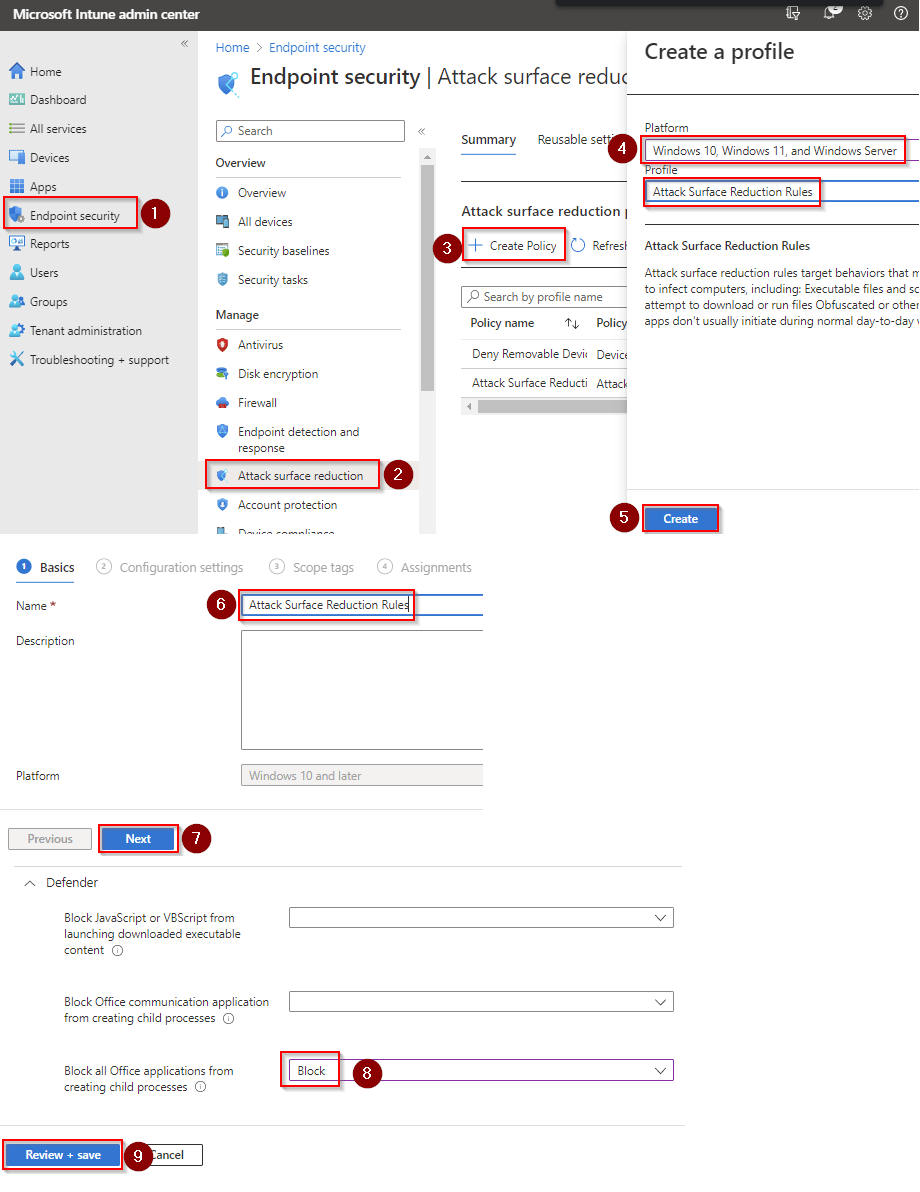
- Go to Microsoft Intune admin center (Microsoft Endpoint Manager) > Endpoint security > Attack surface reduction > Create policy.
- Set platform to Windows 10, Windows 11, and Windows Server.
- Set Profile to Attack surface reduction rules.
- Set the Name and click Next.
- Set Block Win32 API calls from Office to Block. Click Next.
- Add your inclusions and exclusions. Click Next > Next > Create.